THIS REPOSITORY IS DEPRECATED.
ALL OF ITS CONTENT HAS BEEN UPDATED AND MOVED TO awesome-pentest-cheat-sheets
Awesome Pentest Cheat
Sheets 
Collection of cheat sheets useful for pentesting
Contribution
Your contributions and suggestions are heartily welcome. Please check
the Contributing Guidelines for
more details.
Security Talks and Videos
General
Discovery
- Google
Dorks - Google Dorks Hacking Database (Exploit-DB)
- Shodan - Shodan is a search engine for
finding specific devices, and device types, that exist online
- ZoomEye - Zoomeye is a Cyberspace
Search Engine recording information of devices, websites, services and
components etc.
- Amass - OWASP Network
mapping of attack surfaces and external asset discovery using open
source information
Enumeration
- enum4linux-ng -
Python tool for enumerating information from Windows/Samba systems
Exploitation
Privilege Escalation
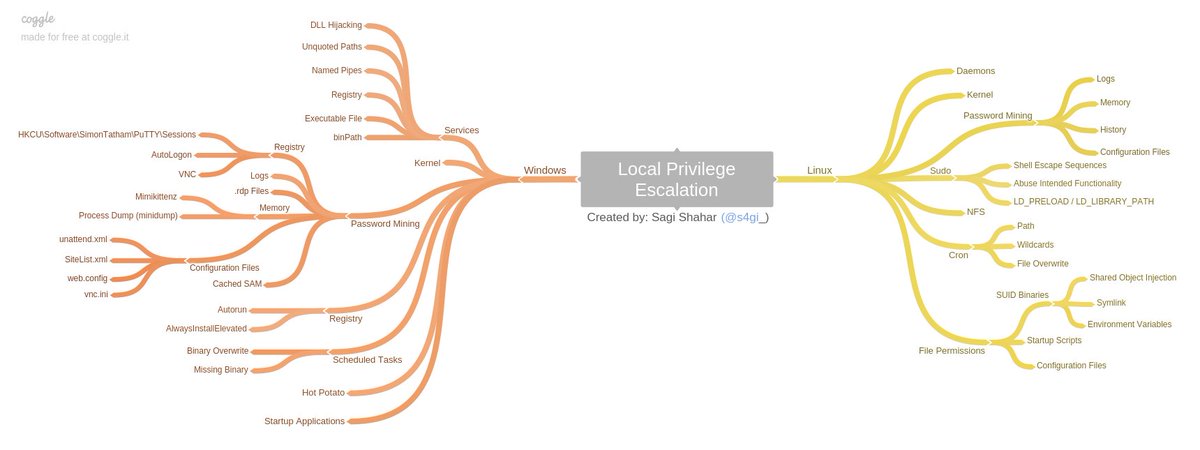
Learn Privilege Escalation
Linux Privilege Escalation
- Basic
Linux Privilege Escalation - Linux Privilege Escalation by @g0tmi1k
- linux-exploit-suggester.sh
- Linux privilege escalation auditing tool written in bash
(updated)
- Linux_Exploit_Suggester.pl
- Linux Exploit Suggester written in Perl (last update 3 years ago)
- Linux_Exploit_Suggester.pl
v2 - Next-generation exploit suggester based on
Linux_Exploit_Suggester (updated)
- Linux Soft
Exploit Suggester - linux-soft-exploit-suggester finds exploits for
all vulnerable software in a system helping with the privilege
escalation. It focuses on software packages instead of Kernel
vulnerabilities
- checksec.sh -
bash script to check the properties of executables (like PIE, RELRO,
PaX, Canaries, ASLR, Fortify Source)
- linuxprivchecker.py
- This script is intended to be executed locally on a Linux box to
enumerate basic system info and search for common privilege escalation
vectors such as world writable files, misconfigurations, clear-text
passwords and applicable exploits (@SecuritySift)
- LinEnum - This
tool is great at running through a heap of things you should check on a
Linux system in the post exploit process. This include file permissions,
cron jobs if visible, weak credentials etc.(@Rebootuser)
- linPEAS
- LinPEAS - Linux Privilege Escalation Awesome Script. Check the Local
Linux Privilege Escalation checklist from book.hacktricks.xyz
- MimiPenguin - A
tool to dump the login password from the current linux desktop user.
Adapted from the idea behind the popular Windows tool mimikatz.
Windows Privilege Escalation
- PowerUp
- Excellent powershell script for checking of common Windows privilege
escalation vectors. Written by harmj0y (direct
link)
- PowerUp
Cheat Sheet
- Windows
Exploit Suggester - Tool for detection of missing security patches
on the windows operating system and mapping with the public available
exploits
- Sherlock -
PowerShell script to quickly find missing software patches for local
privilege escalation vulnerabilities
- Watson -
Enumerate missing KBs and suggest exploits for useful Privilege
Escalation vulnerabilities
- Precompiled
Windows Exploits - Collection of precompiled Windows exploits
- Metasploit
Modules
- post/multi/recon/local_exploit_suggester - suggests local
meterpreter exploits that can be used
- post/windows/gather/enum_patches - helps to identify any missing
patches
Payloads
Genaral
- Fuzzdb -
Dictionary of attack patterns and primitives for black-box application
testing Polyglot Challenge with submitted solutions
- SecList - A
collection of multiple types of lists used during security assessments.
List types include usernames, passwords, URLs, sensitive data grep
strings, fuzzing payloads, and many more
XSS
Write-Ups
Online
Off-Line
Wireless Hacking
- wifite2 - Full
automated WiFi security testing script
Defence Topics
Programming
pentestcheatsheets.md
Github